Identifiers
Each storage backend has an identifier that is used to reference the storage backend in the configuration, such as when specifying the storage backend for an environment. Identifiers can be any string value but must be unique. Flipt creates adefault identifier and storage backend for you automatically if you don’t specify one.
In the following example, we’ve defined two storage backends:
stagingis a local storage backend that will serve Flipt flag state from a local directory.developmentis a memory storage backend that will serve Flipt flag state from an in-memory store.
Backends
Flipt v2 supports the following storage backends:Local
The purpose of this backend type is to support serving Flipt flag state directly from your local filesystem in a git repository. This allows the the data to be persisted between server restarts. Flipt will periodically rebuild its state from the local disk every 10 seconds.default and serve Flipt flag state from the current working directory.
For guidance on setting up Git repositories with existing feature files, see our Git Repository Initialization guide.
Memory
The purpose of this backend type is to support serving Flipt flag state from an in-memory store. This is useful for development and testing purposes where you don’t want to persist flag state to disk.default and serve Flipt flag state from an in-memory store.
Git Remotes
Flipt v2 supports syncing flag state to and from a remote git repository.staging in memory and will sync flag state to and from the remote repository.
Fetch Policy
Thefetch_policy configuration option controls how Flipt handles connection-related issues when attempting to fetch from a remote Git repository.
Available Policies
-
strict(default): Flipt will fail and return an error if it encounters connection issues when trying to fetch from the remote repository. This ensures that any connectivity problems are immediately visible and must be resolved. -
lenient: Flipt will continue operating even if connection issues prevent fetching from the remote repository. This allows Flipt to remain functional during temporary network issues or remote repository unavailability.
Usage Example
Conflict Resolution
Conflicts can occur when syncing flag state to and from a remote repository. The conflict resolution strategy in Flipt v2 is currently rudimentary and we aim to improve this in future releases. When syncing flag state to and from a remote repository, Flipt will behave as follows:- Remote state is synced to the local storage backend using the configured
poll_interval - On writes to the Flipt server, the local storage backend will create a new commit and push it to the remote repository
- Flipt keeps track of the last commit hash for each storage backend
- If a write is made to a flag state file that has been modified since the last commit, Flipt will refuse to push the changes to the remote repository and will instead return an error
- If a write is made to a flag state file that has not been modified since the last commit, Flipt will push the changes to the remote repository
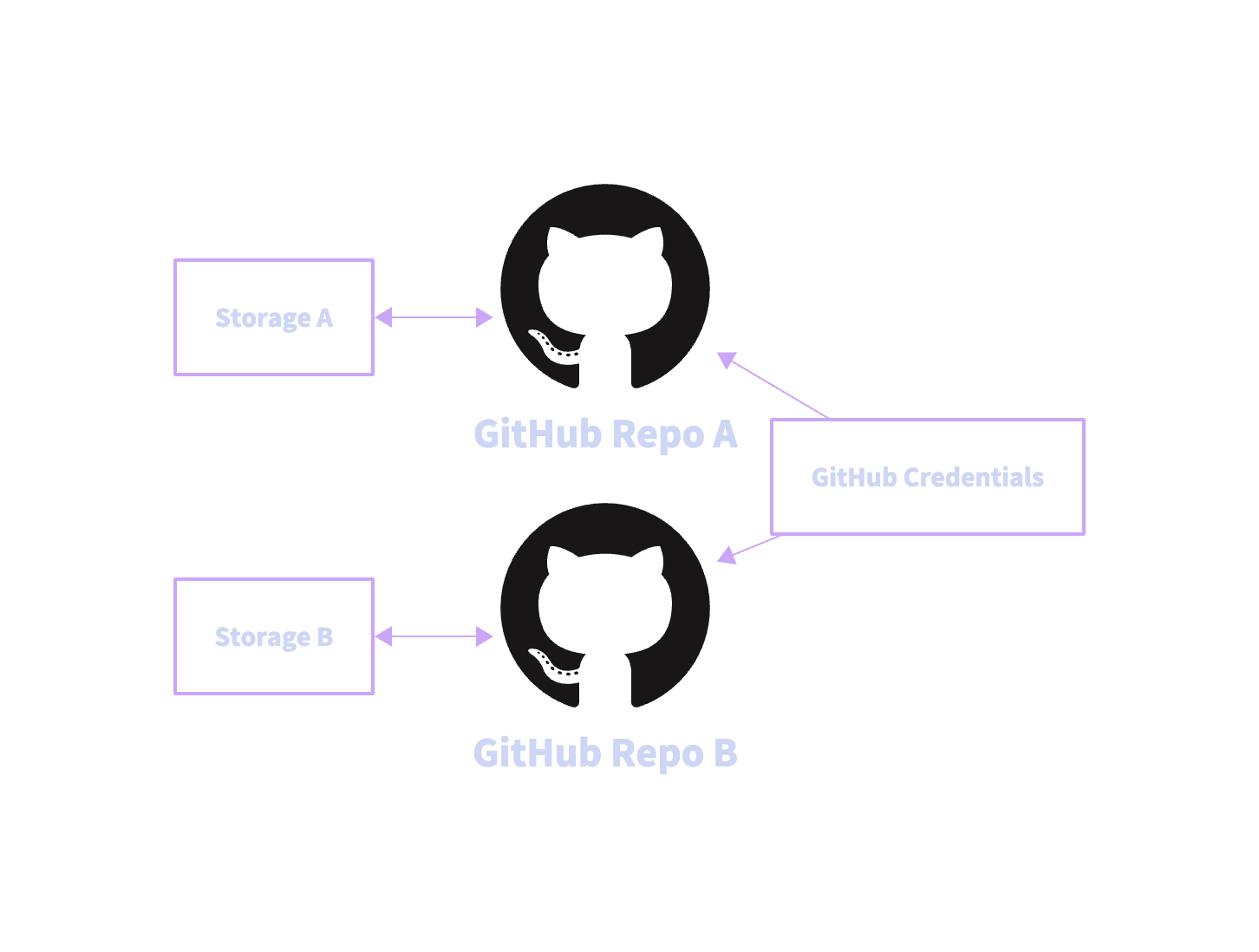
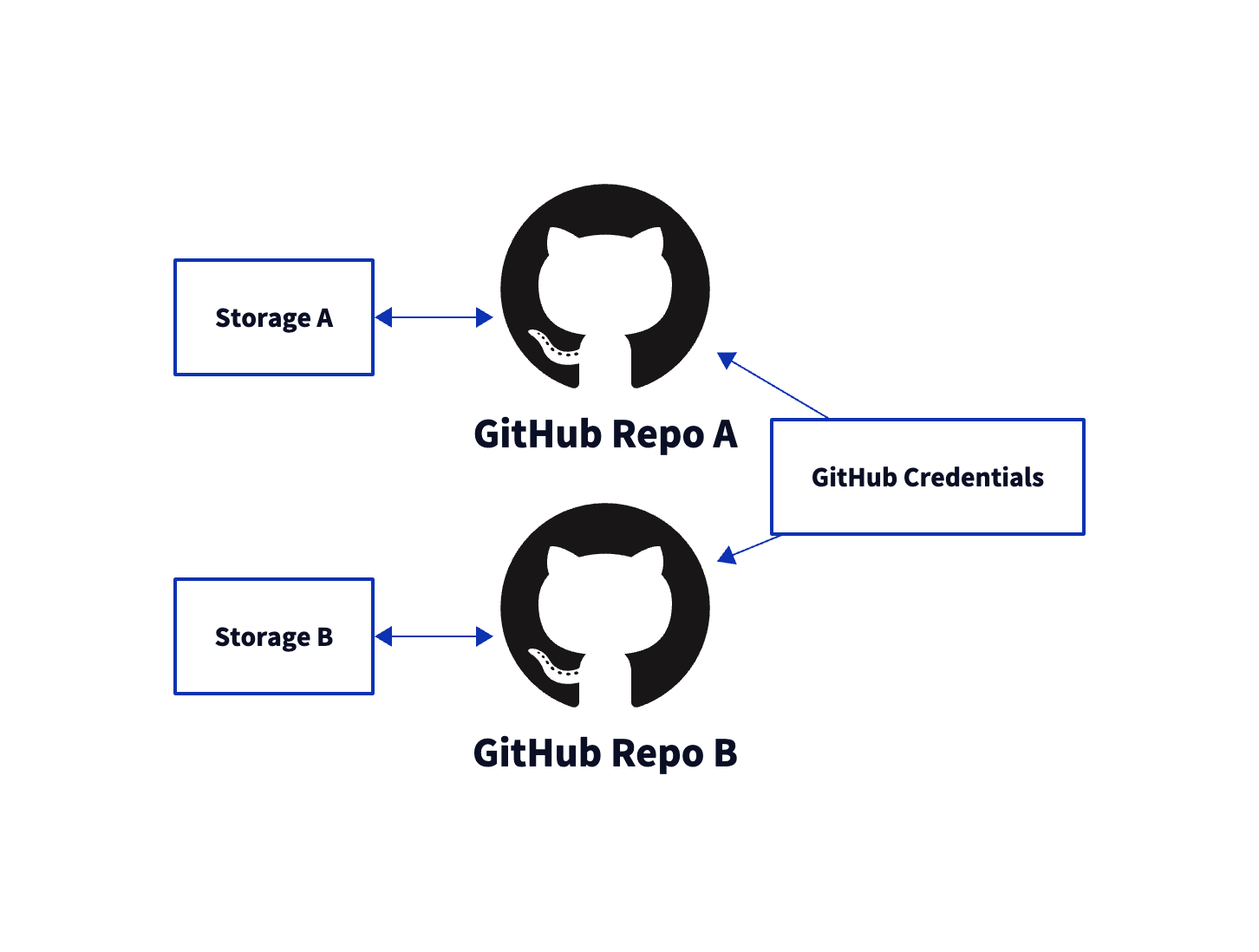
Credentials
Credentials enable the ability to authenticate with remote repositories. Supported authentication schemes are:basicsshaccess_tokengithub_app
credentials configuration section and use identifiers to reference the credentials in the configuration.
Basic
Basic authentication is a username and password pair.SSH
In order to configure a git remote with SSH, you will need to generate an SSH key-pair and configure your repository provider with the public key. GitHub has some excellent documentation regarding how to generate and install your credentials here. Once you have your private key credentials you will need to configure Flipt to use them. This can be done via thestorage.git.authentication.ssh configuration section:
Access Token
Access tokens are a type of credential that are used to authenticate with a remote repository. These can be used for any remote repository provider that supports access tokens such as GitHub, GitLab, Gitea, and Azure DevOps.GitHub App
GitHub App authentication provides a more secure alternative to personal access tokens (PATs) for authenticating with GitHub repositories. GitHub App tokens are short-lived, offer higher rate limits, and provide more granular permissions. To use this credential type, you need to create a GitHub App and install it on your repository or organization. You can provide the private key either as a file path or as raw bytes inline:You must provide either
private_key_path or private_key_bytes, but not
both.